At ProSiebenSat.1, not only are we expanding into digital entertainment and commerce but our TV business is also undergoing digitization. To deliver an excellent and uninterrupted consumer experience, security is crucial. Read on to find out how we secure our business.
Over the past few years, we have noticed an increase in cyber-security threats, as have many other companies. This change is due to the increased digitization of our TV and sales business, the expansion into digital B2C businesses, and the growing number of attacks on competitors and business partners:
Digitization of our TV and sales business: Within the last ten years, more and more proprietary broadcast equipment has been replaced by IT equipment. Content is produced and stored digitally. Ultra-High-Definition (UHD) transmission, interaction with smart devices such as Smart TVs, and demand for high performance network infrastructures will become standard within just a few years. This means that components at all levels need to become more connected in order to automate and speed up production and business. Shifting to modern networked technology might boost efficiency but it also increases the attack surface.
Expansion into digital B2C businesses: As part of the Group’s core business strategy, ProSiebenSat.1 has expanded considerably into digital entertainment and commerce. We promote and accelerate the growth of large platforms such as Parship, Verivox, or maxdome. Unlike the traditional TV business, they are business-to-consumer (B2C) focused and operate online services on which thousands of users rely. On these platforms, our customers’ data must be protected, and resilience against threats such as Denial of Service (DoS) attacks must be ensured.
Attacks on competitors and business partners: In the last couple of years, we have witnessed successful attacks on business partners and competitors. Widespread ransomware infections affected many companies, resulting in lost business and considerable time and expense being spent on the clean-up. Attackers managed to take control of several social media accounts run by the French TV station TV5Monde, and caused severe threats to the station’s playout operations. Attacks on producers such as Sony and HBO lead to the unwanted release of valuable assets and/or interruption to business. Such incidents remind us to remain alert.
These developments have prompted us to put more emphasis on cyber-security. When it comes to cyber-security, we strive for a holistic approach. The reason is simple: Any given security system is only as strong as its weakest link. This is why, from our point of view, it is crucial to focus just as much on people as on processes, and technology
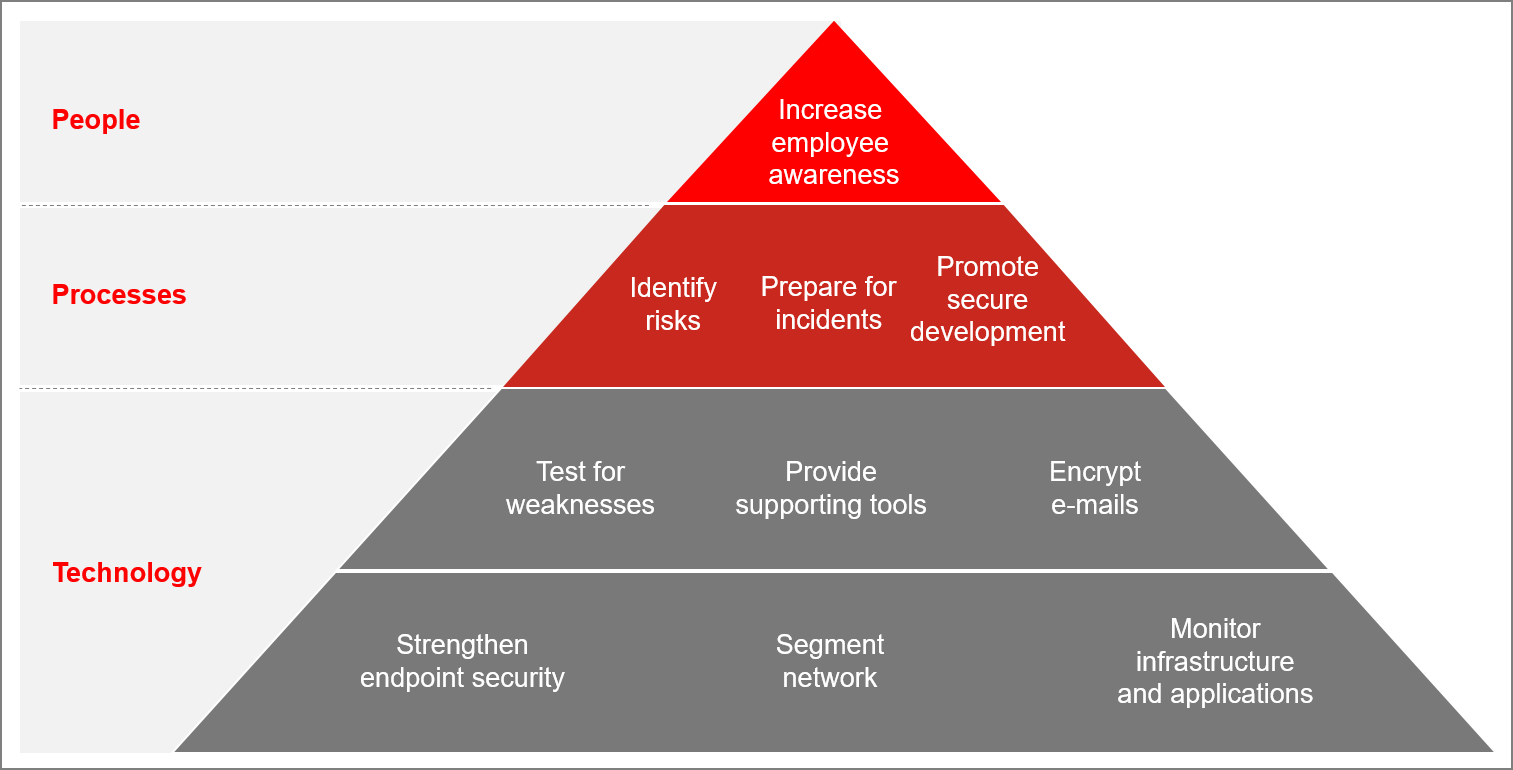
These are our top 10 actions for strengthening our cyber-resilience:
1. Increase employee awareness: At ProSiebenSat.1, we are proud of our open, friendly, and connected culture. To prevent unnecessary incidents, it is essential to make people aware of potential threats and explain how to use technology effectively. We want to share information securely to maintain our open-minded and communicative attitude as a key asset and enabler for our strategies. To make learning more fun, we have a web-based interactive training with game-like look and feel. In addition, almost all our managers have participated in face-to-face briefings.
2. Systematically identify risks: To set the right priorities in IT, you need to understand your business, its potential risks, and where technology plays a crucial role. Therefore, we systematically analyze our business processes: We evaluate the needs of our business regarding confidentiality, integrity, and availability, and determine the key applications for our business processes. As an example, one analysis revealed that there was a particular sales application that needed to be a priority in terms of security. Without this analysis, this application may have not received the appropriate attention because it otherwise runs very smoothly and does not represent an investment priority for business or IT. In a second step, any critical applications that have been identified are then systematically analyzed for security weaknesses.
3. Prepare for incidents: Try as you might, you will never be able to guarantee 100% security and prevent every conceivable kind of incident or breach. Nevertheless, we aim to be prepared for as many eventualities as possible. To that end, we defined escalation processes as well as response plans for various cyber-breach scenarios. To enable our teams to utilize them in case of an emergency, war games are being conducted at each unit.
4. Promote secure development and architecture: Ideally, not only do we want to detect security incidents when they occur, but actually prevent them from happening in the first place. To do so, security needs to be integrated in the design and development of new systems. During the development of a new system, we review its architecture from a security perspective. We have developed practices for secure coding and are investing in expanding our engineers’ capabilities in secure coding. The next step is to align security testing more tightly with our continuous integration (CI) pipeline to turn security into a good habit rather than a one-time project.
5. Test for weaknesses: We know that nobody is infallible. To test crucial applications for weak spots, we run different kinds of penetration tests to determine potential weaknesses. First, we perform generic tests from the perspective of an outsider which focus on services that can be accessed from the web. Open standards like those from OWASP, NIST, SANS, etc. serve as good benchmarks for us. Second, we run specialized tests within our network. For example, we may try to compromise our playout signal from a client within our own network. The tests need to cover relevant threat scenarios, need to be sufficiently advanced to detect weaknesses, but of course they also need to be set up carefully so as not to endanger ongoing operations. To promote an adequate patch level of our IT systems these activities are supported by regular scans within our infrastructure for known vulnerabilities. Of course, there are zero-day exploits, but timely patch management is crucial to prevent successful attacks by malware such as WannaCry, or mitigate risks resulting from vulnerabilities like Meltdown or Spectre.
6. Provide supporting tools: To support our staff in managing information securely, we have introduced a variety of tools for collaborative work, wherever we are. Accompanying these new technologies, we offer password managers, screen privacy filters, or encrypted USB sticks to protect information while traveling. We have found the combination of user-friendly tools with increasing employee awareness to be very effective.
7. Encrypt e-mails: As e-mail still represents the number one communication tool – including exchange of confidential information with third parties – we are fostering the establishment of background e-mail encryption with key business partners. This easy but at the same time effective step helps us to secure sensitive communication e.g. when we work on merger & acquisition deals with legal advisors.
8. Strengthen endpoint security: We regularly observe attacks on our infrastructure and receive an average of 14 million spam e-mails each month. Spear fishing campaigns to commit “CEO fraud” have also become increasingly common. As other companies are, despite modern anti-virus technology, we are also challenged by the evolving threats of ransomware and other malware. We can mitigate these threats, but are aware that attacks do not stop at the perimeter of our network. Therefore, we evaluate and implement advanced threat protection solutions.
9. Segment network: Besides the usual server and client infrastructure of a large company, we have high demands on throughput to handle all our large media files and streams. We work hard to maintain a high-performance infrastructure. At the same time, we isolate parts of the network to protect critical assets like playout systems. To do so, we make use of classical techniques like state-of-the-art firewalls, design network security zone concepts, and integrate modern solutions such as SaaS and container architectures.
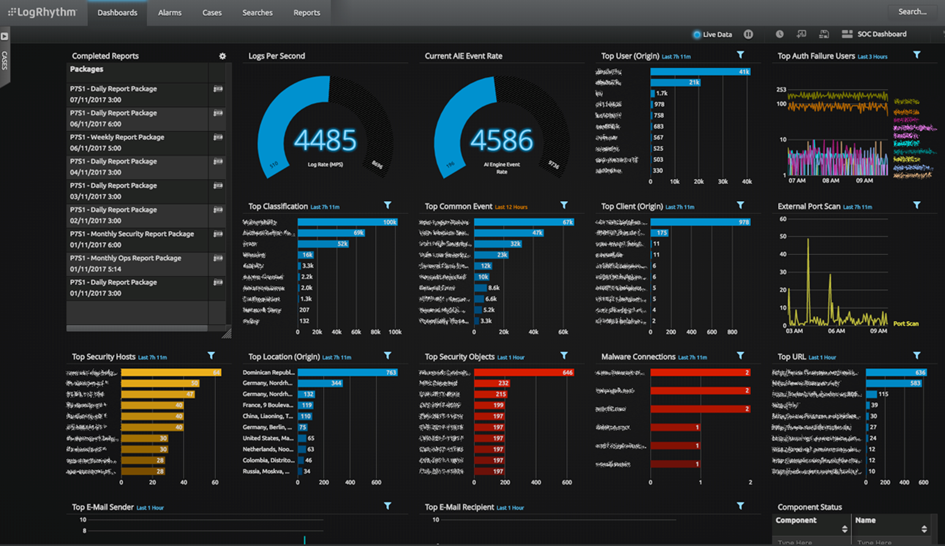
10. Monitor infrastructure and applications: To detect fraudulent behavior, a security information and event management (SIEM) tool allows effective monitoring of infrastructure and applications by correlating heaps of events detected within our network. Setting up and operating a tool like this requires effort and dedication. We believe that such central monitoring is worth it, since it allows for fast and efficient detection of attacks by our analysts.
 We do our best to provide security for ProSiebenSat.1 so that our consumers can enjoy our services without interruption. We would also like to think that you have found inspiration in this article on potential focus areas for your security strategy.
We do our best to provide security for ProSiebenSat.1 so that our consumers can enjoy our services without interruption. We would also like to think that you have found inspiration in this article on potential focus areas for your security strategy.